SYSTEM SERVICES
FOR IT INFRASTRUCTURES
Optimize your IT infrastructure with our advanced system services and solutions for businesses.
We help define the client's IT infrastructure starting from a study of their actual needs.
Experience, but not standardization.
We've been working in the IT industry for over 40 years, but our approach has never become impersonal. On the contrary, we support each company with a direct, ongoing, and concrete relationship.
We don't offer off-the-shelf solutions; we work with our clients to design the best possible infrastructure, taking into account their specific operational needs, context, and growth objectives.
Our approach begins with an in-depth analysis of the client's specific needs, allowing us to design an optimized and tailored IT infrastructure.

Integrated Cyber Security
We protect data, users and applications at every level, wherever they are
CYBERSECURITY
Modern security requires distributed architectures capable of protecting data, users, and applications wherever they are. Technologies like SASE and XDR allow you to extend the defense perimeter and automate threat response at every level: network, endpoint, and workload.
- We implement Zero Trust architectures with centralized control
- We configure SASE environments for secure remote access and distributed policies
- We install XDR systems for automatic detection and response to attacks
- We manage firewalls, endpoint protection and behavioral analytics
- We optimize access to cloud applications via SD-WAN and secure tunnels
- We provide centralized visibility and control over users, devices, and traffic.
SECURE ACCESS SERVICE EDGE (SASE)
The SASE model unifies network security and connectivity for users, locations, and distributed applications. By integrating access control, traffic inspection, and WAN optimization in the cloud, it transcends the limitations of the traditional perimeter and ensures secure performance wherever users are located.
- We design scalable SASE architectures that can be integrated with existing infrastructure
- We configure granular access policies, traffic inspection, and DNS filters
- We optimize access to cloud applications via SD-WAN and secure tunnels
- We provide centralized visibility and control over users, devices and traffic
NETWORKING
AND ACCESS
Modern corporate networks must be scalable, segmented, and secure. Centralized management and controlled access are essential to ensure continuity and security, even in distributed or multi-site environments.
- We design scalable LAN/Wi-Fi with segmentation and VLANs
- We install access points, intelligent switches and NAC solutions
- We manage access and authentication policies at the network level
- We centralize control of devices and users
Visibility, Continuity and Control
We monitor, detect, and respond to anomalies before they become problems
PROACTIVE MONITORING
Proactive monitoring allows you to maintain visibility into every infrastructure component, detect anomalies in real time, and prevent failures. Modern solutions offer centralized supervision and automated alerts.
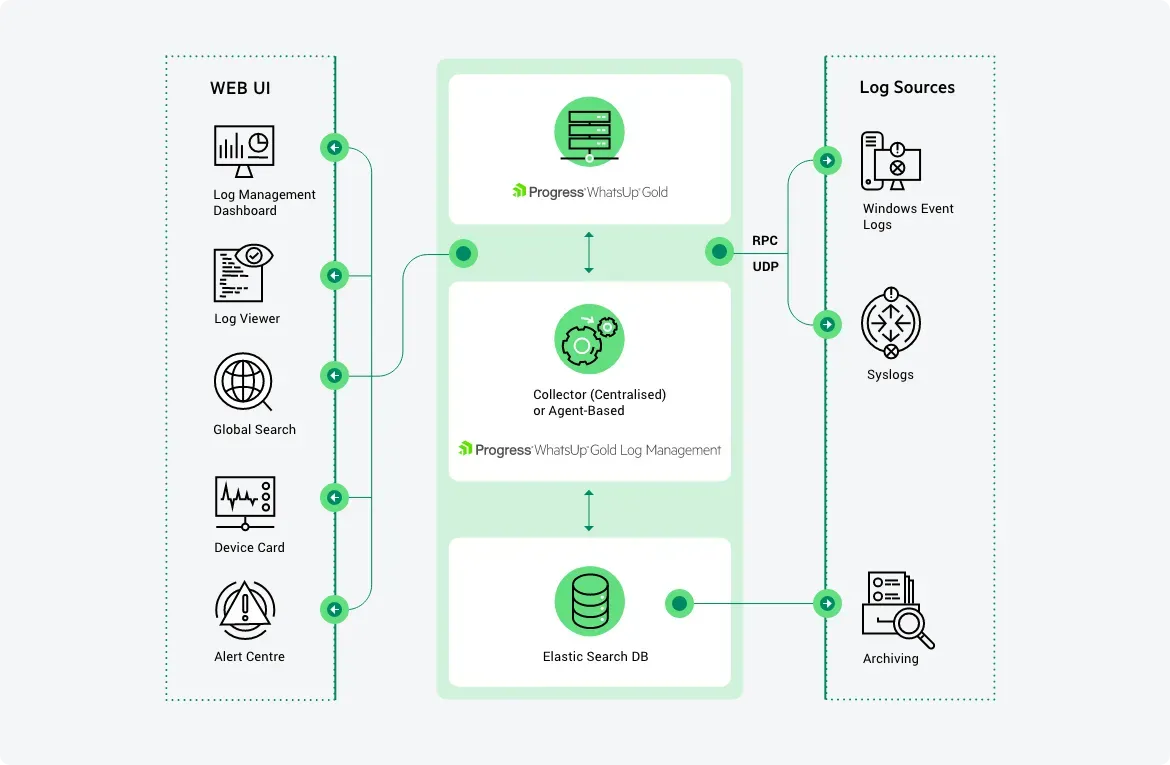
- We configure network, server, storage and application monitoring
- We define thresholds and rules for the automatic detection of critical issues
- We activate dashboards and reports for technical and management visibility
- We integrate the system with multi-channel notifications and alerts
Real case: unmonitored switch
A medium-sized company experienced a network outage on May 12 at 3:00 AM due to an unmonitored access switch crashing.
The lack of SNMP, logs, or heartbeat prevented automatic detection. It wasn't until 8:30 AM, when staff arrived, that the alert was triggered.
It took the IT team an hour to identify the fault: over 6 hours of total downtime and 25 man-hours of lost productivity.
With an active system (e.g. WhatsUp Gold), the anomaly would have been detected and reported immediately.
BUSINESS CONTINUITY AND RECOVERY
Business continuity requires precise replication, failover, and recovery strategies to ensure constant service delivery, even in the event of a failure or incident. Modern solutions enable real-time protection and periodic recovery testing.
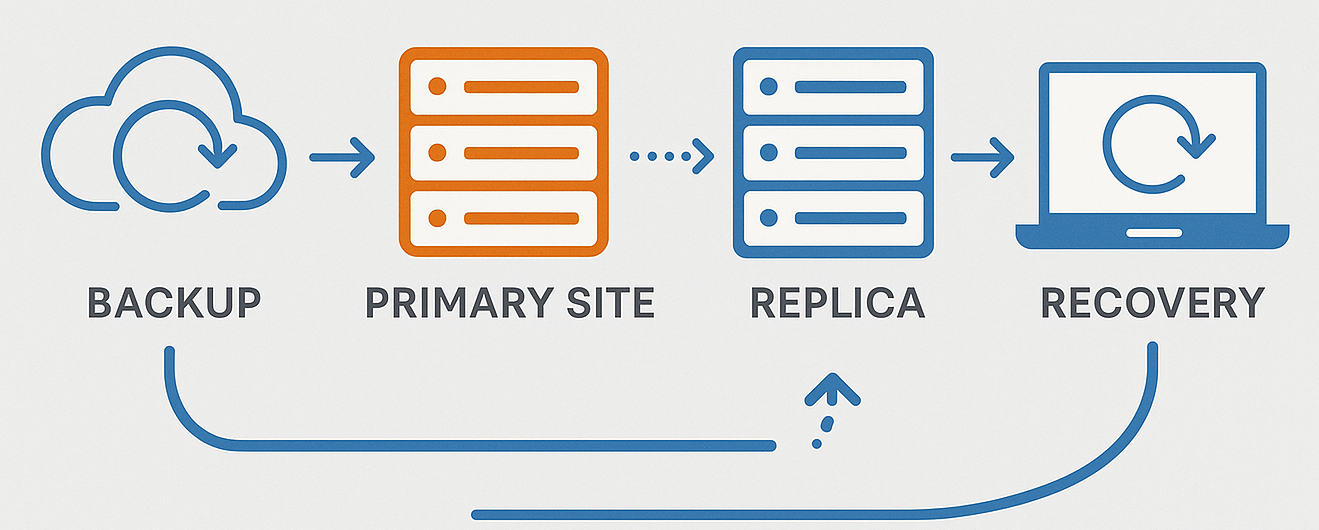
- We design and implement automatic failover systems
- We configure synchronous or asynchronous replications on secondary infrastructures
- We automate backup and recovery of virtual environments
- We perform controlled recovery tests with documented reports
Virtual Infrastructure and Corporate Networks
We build scalable, resilient and interconnected IT environments
VIRTUALIZATION AND DATA CENTER
Virtualized architectures enable you to consolidate physical resources, increase efficiency, and ensure operational flexibility.
Centralized workload management and dynamic scaling are the foundation of modern data centers.
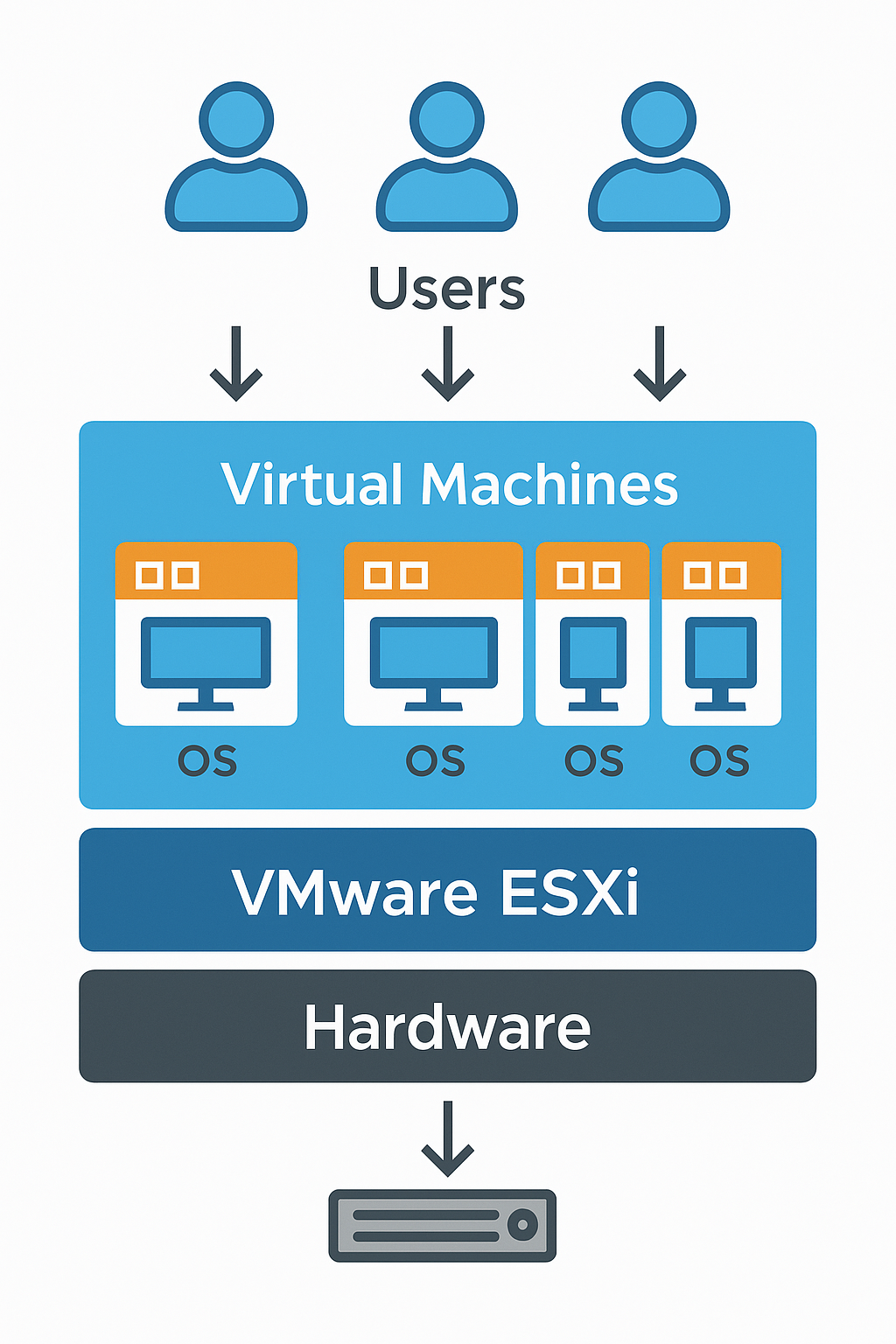
- We design highly available virtualized environments
- We configure clusters, shared storage, and load balancing
- We automate resource provisioning
- We ensure VM security, isolation, and performance
Hybrid Cloud and Operational IT Services
From cloud to day-to-day support, everything you need to keep your business running.
HYBRID CLOUD AND PRIVATE CLOUD
Private and public cloud integration enables efficient load distribution while maintaining control over sensitive data. Hybrid architectures offer scalability, flexibility, and regulatory compliance, with unified management.
- We design private cloud environments on a virtualized basis
- We extend public cloud resources for specific needs
- We automate provisioning, balancing and monitoring
- We ensure continuity and security in hybrid environments
Complete IT Infrastructure Management
Not just technology: daily management, real support
Technical Support and Help Desk
- Telephone, remote, and on-site technical support
- Quick resolution of software and hardware issues
- Proactive monitoring and ticket management
- User support on operating systems, apps and configurations
Hardware Supply and Management
- Direct resale of professional IT devices (PCs, servers, networking)
- Tailor-made hardware solutions for every operating context
- Integrated provisioning and initial configuration
Servizi IT in Outsourcing
- Complete delegation of technical and systems support
- Centralized management of devices and equipment
- Administration and maintenance of corporate IT systems
Request a personalized consultation for your IT infrastructure
From cybersecurity to technical support, from data management to cloud environment design, our team is at your side to build truly customized IT solutions.
With over 40 years of experience, we don't offer standard solutions, but rather support each client with a direct, consultative approach. Every company is unique. So is every project.
Tell us your needs. We'll help you turn them into solutions.

For over 40 years, we have been supporting leading Italian and international companies with customized IT services and solutions.
Optimize Your Infrastructure:
Experience beyond borders, with the same solidity.
To ensure continuity and consistency in our services, we also operate in Switzerland through Sysdat International SA, headquartered in Stabio. This allows us to offer local support to companies in the Canton of Ticino, while maintaining alignment with the Sysdat Group's technological and methodological standards.
Reference brand: world-leading solutions
When designing IT infrastructures, we use proven and reliable technologies from leading global vendors:
- Cybersecurity: Fortinet, Cisco, SentinelOne
- Hardware e server enterprise: HPE, Dell
- Virtualization: VMware, Microsoft Hyper-V
- Ambienti cloud: Microsoft Azure, Amazon Web Services (AWS), Google Cloud Platform
- Infrastructure Monitoring: WhatsUp Gold














